Now that you have acquired the image of the USB drive, you will want to analyse the image.
You will use Autopsy 4.9.1 to analyse the image and show what Autopsy
can offer. This is a chance for you to understand the basics of the software allowing you to
know where you are able to find the data you need when conducting analyses.
Open Autopsy. Go to MAIN MENU > Forensic Tools > Autopsy. Choose "New Case" from the popup menu.
It will prompt up asking for a "Case Name", so give it
meaningful name such as Lab1. "Base Directory" is where
your case will be saved - choose HOME directory /home/caine. Leave everything else as it is. Click "Next".
-
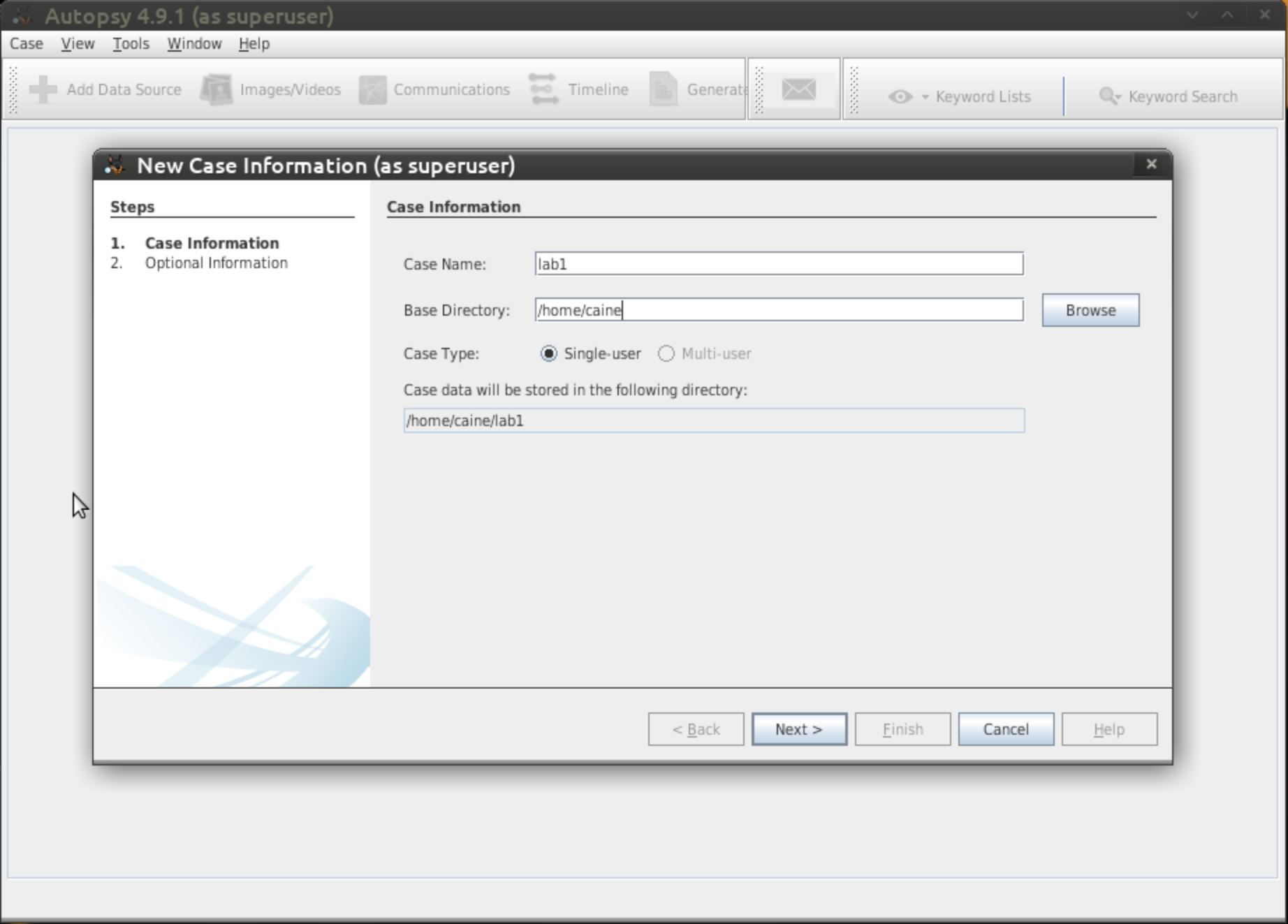
- Figure 3: Case Information
As this is your first case, make the case number 001. As the
examiner, fill your full name in and then click "Finish".
Autopsy will start creating a database of your image. This
may take a couple of minutes.
-
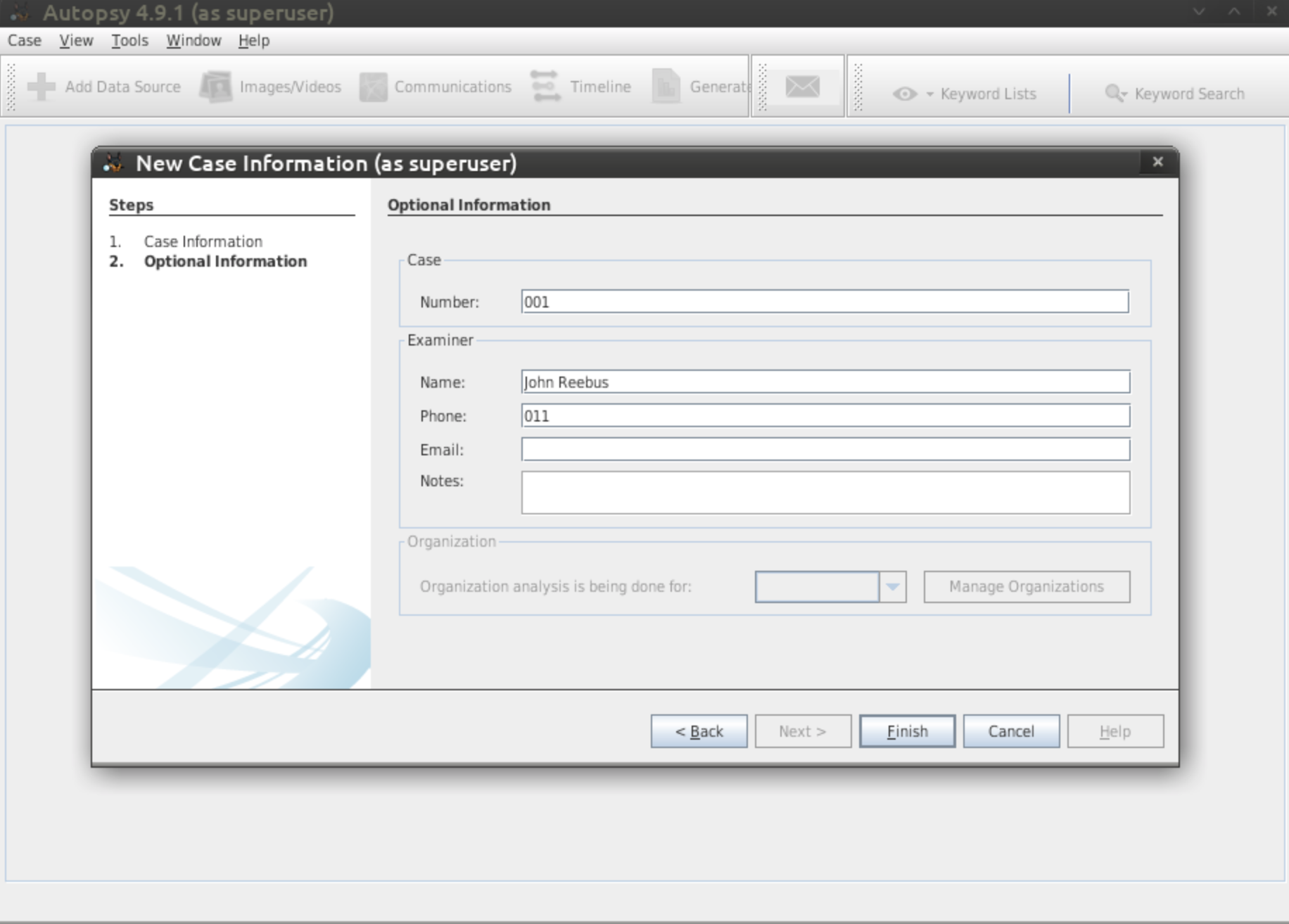
- Figure 4: Operational Information
Once created, it will ask you to select your data source. Click "Disk Image and VM file" to
add your disk image.
-
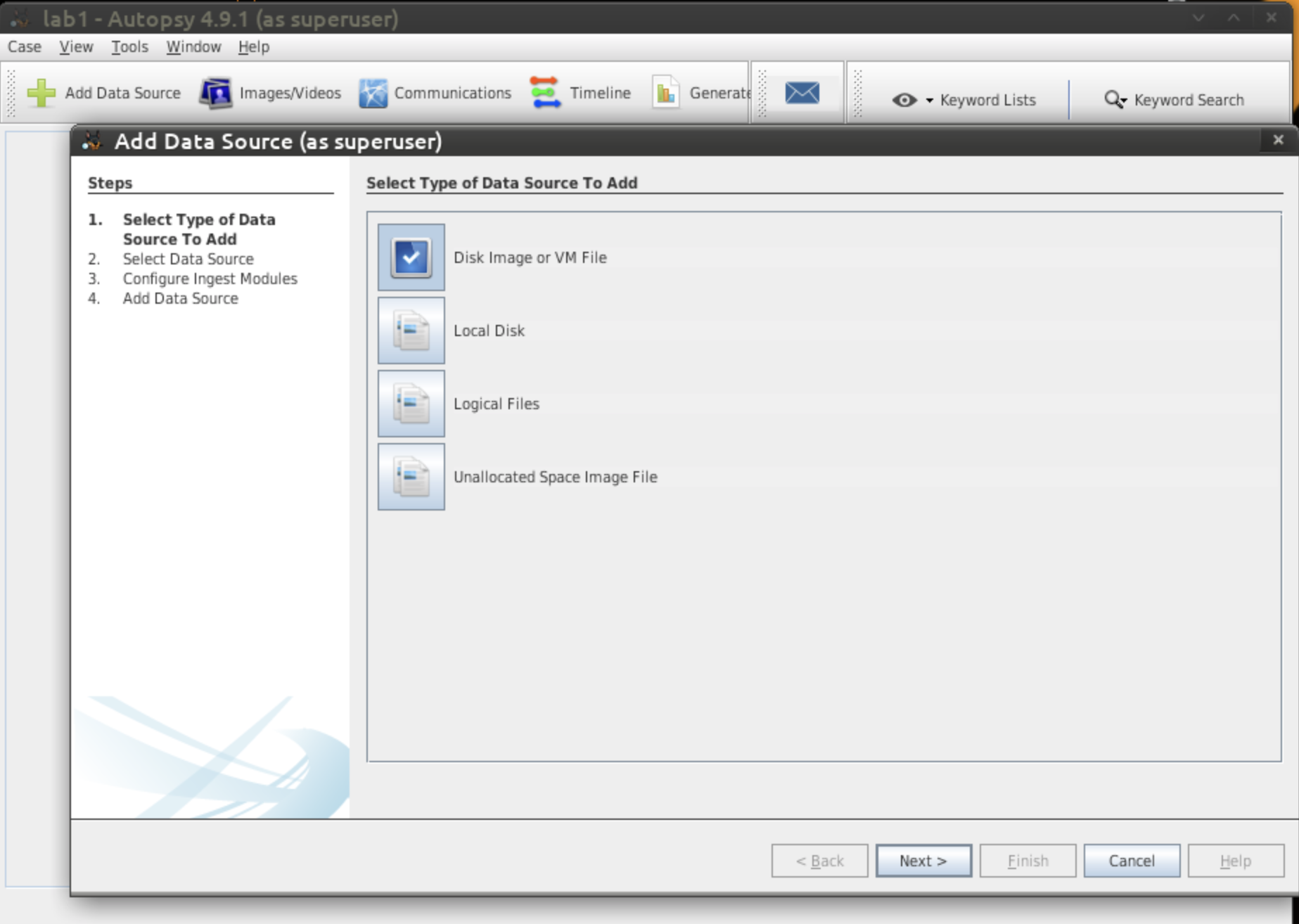
- Figure 5: Data Source
-
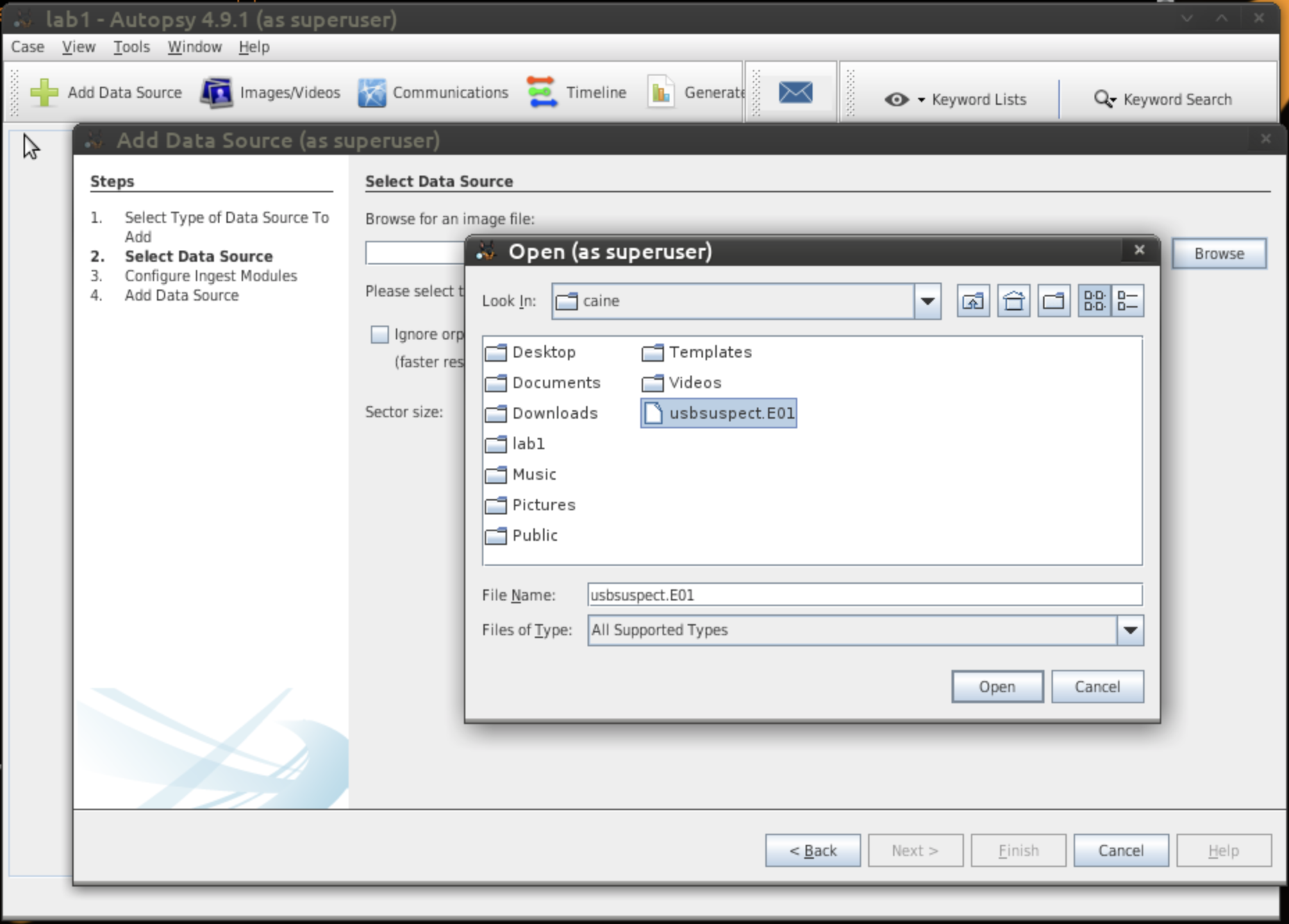
- Figure 6: Select Data Source
Choose the modules that you want to ingest.
For this lab Select All. Click on Keyword Search and select all
available keyword lists. Click "Next", then "Finish".
-
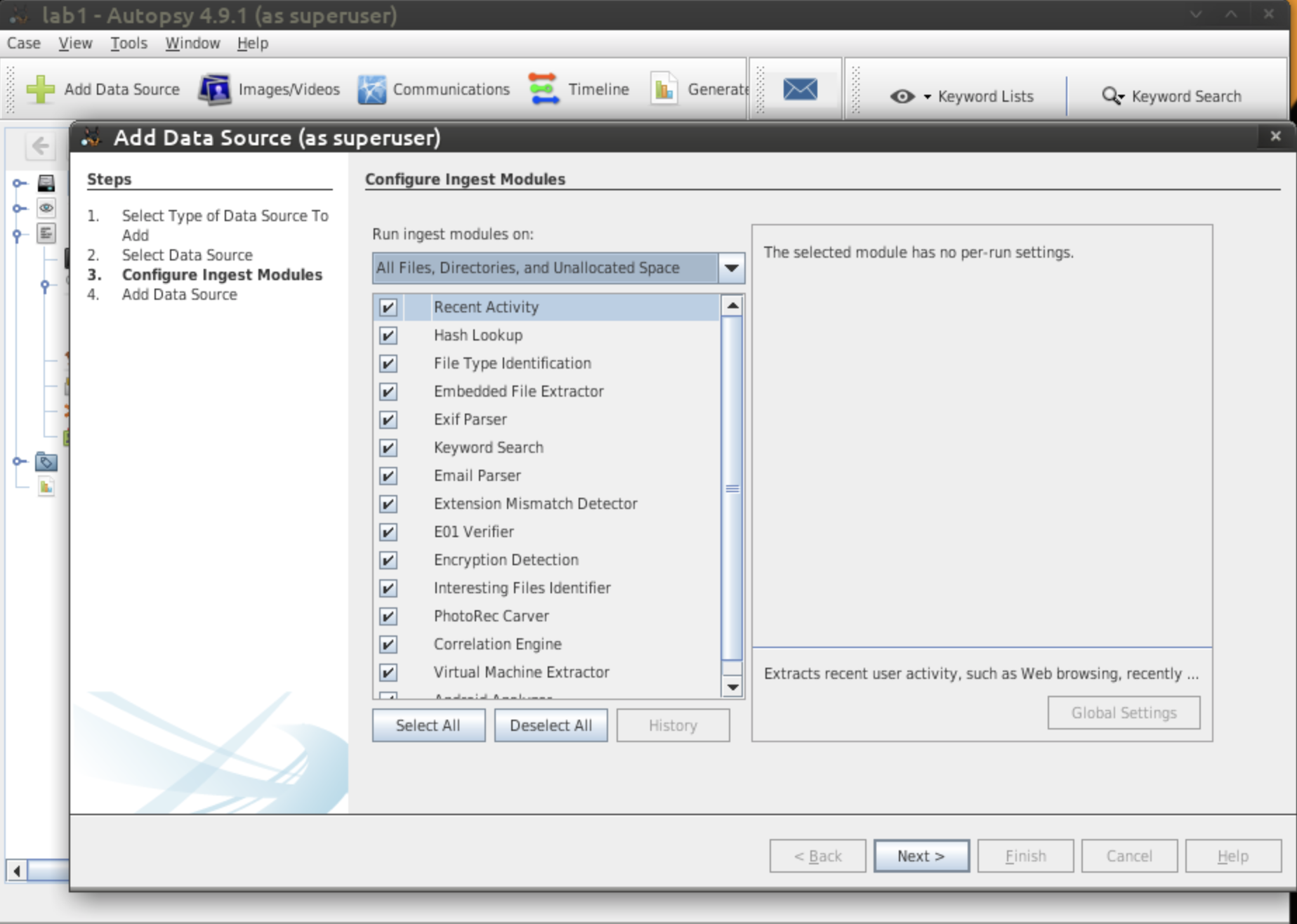
- Figure 7: Modules
Running all the ingest modules will take a few minutes. In the bottom right, watch the progress.
While you're waiting, Have a look at the Autopsy Quick start guide at:
Autopsy User Guide. It gives you a
brief explanation of the ingest modules and some example uses cases.
Once the ingestion is completed, you will see the interface as shown below. On the lefthand side is the "Tree View". It shows the saved results from the automated ingested
modules you have selected. The "Result View" is on the top right, it shows the details
after selecting something from the "Tree View". There will be options to choose to show
different formats. On the bottom right there is the "Content View". It shows files in
different formats and there are tabs to choose to view the file in different ways. To show
data in this area, a file must be selected in the "Result View".
-
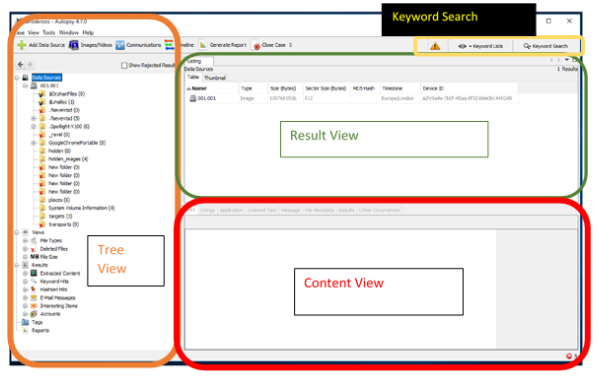
- Figure 8: Autopsy View
Take some time to explore the different results in the tree and see what you can find.
For example, you should be able to see what files the suspect has deleted, and, in
some cases, you will be able to extract the file and view it if you want.
If you navigate to "Extracted Content", it will show you web contents which the suspect
has been browsing. Have a look at each one and click into a URL. It will show you a lot of information. Look at the highlighted area, explore this
area yourself. For example, look at "YouTube".