If you can see this check that
Firewalls + Security
Firewalls
Firewalls
- Firewalls and the implementation of Management Policy plus proactive security methods
- Management Policy can include
- Network Services allowed to run, and under what conditions
- Client access to external resources
- Quality of service
- Security and maintaining availability
Corporate Firewalls
- Cisco PIX
- Cisco router ACLs
- Linux router iptables
- PIX syntax is strange, yet PIX solutions are popular!
- ACLs are weak for policy implementations
- iptables is powerful but uncommon.
Linux Firewalls
- Security issues which Linux firewalls can deal with:
- Denial of service
- Differences between external and internal users
- Hiding local-only services
- Traffic management
- Virus and hacking protection
- Implementing management policy
- Rules are needed in terms of packets arriving, leaving, and passing through.
iptables
- Since kernel 2.4, the standard interface for firewall configuration is iptables.
- It implements its rules using many "tables"
- Filter - handles standard "firewall" things
- NAT - rewriting of source/destination IPs
- Mangle - specialised hacking of packet info
- RAW - low-level modifications to packets
- Most firewalls only need to be involved with the filter table
Chains
- Within each table is a number of chains.
- Think of each table as containing different types of rules you might want to use (like "filter" rules).
- Think of chains as defining WHEN a packet will have those rules applied to them.
- Chains are done in a particular order.
- Some packets only go to some chains and not others (depending on how the packet was made).
Chain Names
- Some chain names you might see are
- PREROUTING
- INPUT
- OUTPUT
- FORWARD
- POSTROUTING
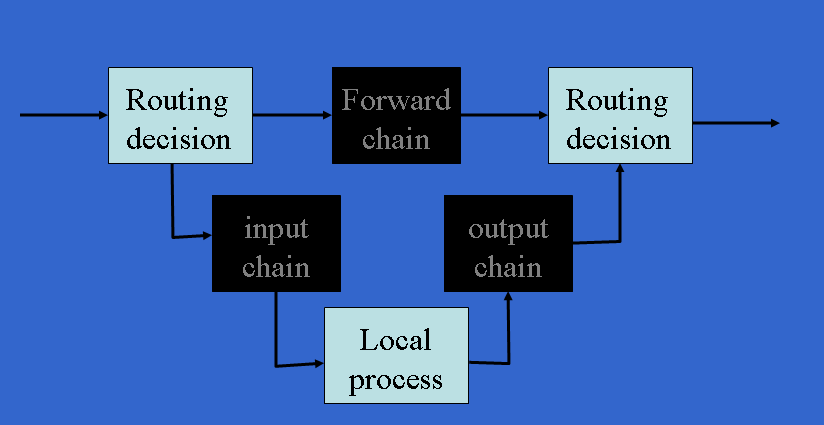
- Summary of the tables and chains a packet will traverse in iptables.
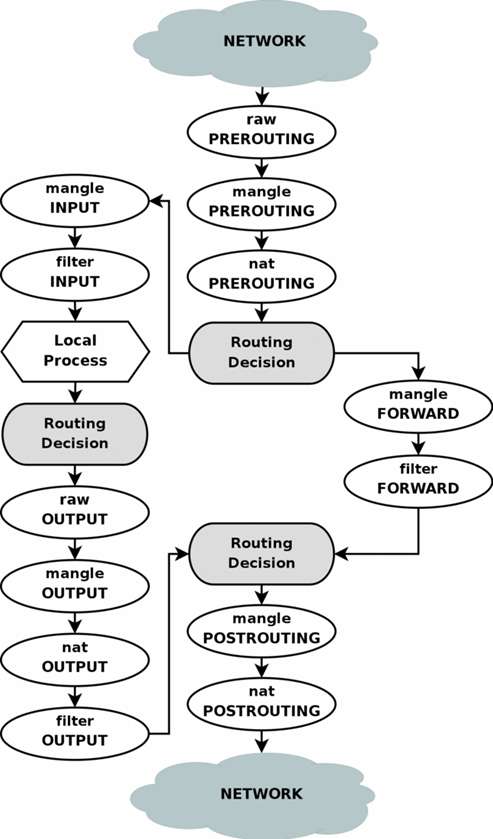
FILTER TABLE CHAINS: INPUT, OUTPUT, FORWARD
FILTER TABLE
- In the filter table a packet will only go through 1 chain.
- Packets created within the computer go through OUTPUT
- Packets which need to be routed from one eth device to another eth device go through FORWARD.
- Packets received by the computer for processing locally go through INPUT
A Chain
- Each chain is made up of 0 or more rules.
- A rule is a set of tests and an action.
- If the tests are all true then the action is performed.
- If a test is partially or completely false then the next rule is looked at instead.
- If all the rules are used up without an action taking place, then the chain POLICY is done instead (i.e. a default rule).
Tests
- Each rule has 0 or more tests.
- There are many tests possible, such as:
- Is this TCP?
- Is this from 10.0.0.5?
- Is this from port 22?
- Is this going to port 23?
- Is this going to ip 50.0.0.1?
- Am I receiving packets faster than 10 per second?
- Which interface is it going out/in on?
- Remember you can combine these tests, e.g. TCP and from port 22.
Actions
- If all the tests are true then the action is carried out.
- Some actions are terminating, meaning that once they are done no more rules are looked at.
- A few actions are non-terminating. This is useful if you want to say print a message if the test is true, but continue on with the next rule anyway.
- Example actions are:
- DROP - delete a packet immediately and terminate
- ACCEPT - the packet is good and terminate
- REJECT - delete the packet and terminate, but send back an ICMP message to the sender
- LOG - print to syslog a message and move onto the next rule.
Some tests:
- Is this TCP ? -p tcp
- Is this from 10.0.0.5? -s 10.0.0.5
- Is this from port 22? --sport 22
- Is this going to port 23? --dport 23
- Is this going to ip 50.0.0.1? -d 50.0.0.1
- Is this going out on eth0? -o eth0
- Is this coming in from eth0? -i eth0
Setting the policy
$ iptables -P INPUT ACCEPT
$ iptables -P OUTPUT ACCEPT
$ iptables -P FORWARD DROP
- This is a typical unsecured machine configuration. Typical machines only have 1 eth device, so don't forward. Otherwise, all packets are allowed.
Editing firewalls
- iptable does allow you to edit firewalls dynamically.
- However, this is very problematic and difficult.
- Instead, I recommend putting all your rules in a file and running that file to change the firewall.
- This allows you to use your favourite editor to write the firewall.
- At the start of the file, delete all current firewall rules in each table using "-F".
$ touch firewall
$ chmod +x firewall
$ vi firewall
/sbin/iptables -F INPUT
/sbin/iptables -F OUTPUT
/sbin/iptables -F FORWARD
# Set the default policies for the chains
/sbin/iptables -P INPUT DROP
/sbin/iptables -P OUTPUT ACCEPT
/sbin/iptables -P FORWARD DROP
- To load these rules do
$ ./firewall
- However, don't do that yet. The default is DROP for INPUT. Without more rules you will be kicked out of the server never to return...
- This is bad if the server is 5 minutes walk away. But if it is 500miles away you are in trouble!
- This type of firewall is INGRESS ONLY. No rules for going out (OUTPUT/EGRESS). Kind of like the XP firewall...
Basic client machine
sport or dport
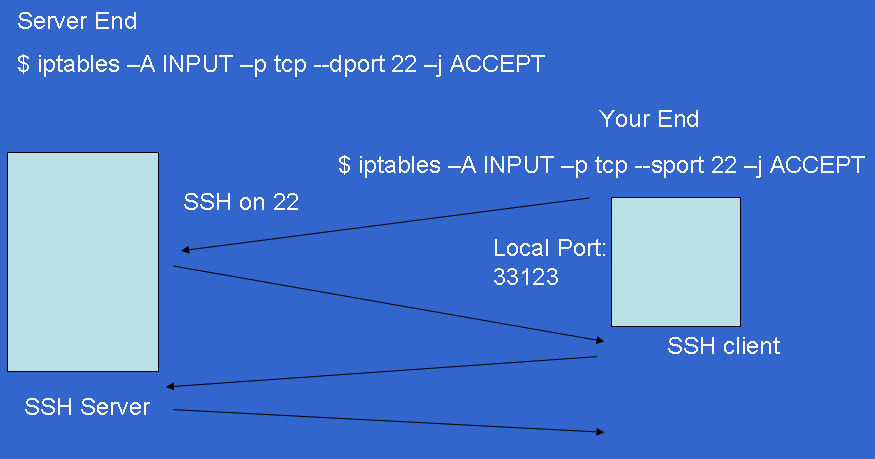
Basic client machine
Add a rule to permit ping
Add a rule to permit safe ping
Monitor safe ping
Monitor Monitor safe ping
Learning firewalls
Basic client machine
Basic client machine
Monitor Monitor safe ping
INPUT ACCEPT
- To be clear, a policy of ACCEPT is seriously silly...
- Good to learn on but wide open to attack.
- ACCEPT policy means you need rules to block. Anything you didn't think about is accepted.
- DROP policy means you need rules to allow. Anything you didn't think about is dropped.
- Security relies on a good policy, and that must be DROP.
DROP or REJECT
- DROP just blocks the packet.
- REJECT blocks and also sends an ICMP message to the sender saying it is blocked.
- DROP gives nothing away, and a hacker finds it difficult to get useful information about your network if packets are dropped.
- REJECT gives away information about your firewall ruleset.
- With DROP and IP, where packets are lossy, some protocols may retransmit a packet which you have dropped thinking it has been lost. This means dealing with the same packet again and again.
- A good rule: intranet traffic should be REJECT, internet traffic should be DROP.
subroutines
- Sometimes, complex rules in a single chain are difficult to manage.
- My server firewall has 200 rules...
- In the same way as programs benefit from subroutines, so do firewall rules.
- Subroutines are created with -N, deleted with -X, and can be reached with a target of "-j subroutinename" and returned with a target of "-j RETURN".
Monitor Monitor safe ping subroutine
Extra tests
- There are many other simple tests.
- Use man iptables to find more
- For example:
Stateful Firewalls
Established: Stateful Firewall
- In TCP/IP, TCP goes through a number of states:
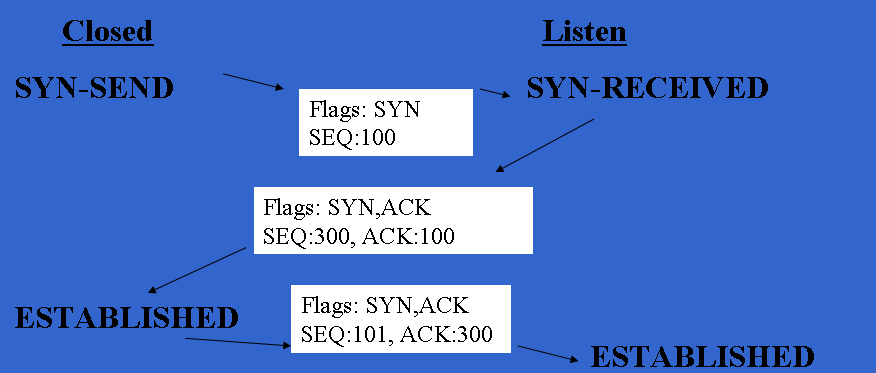
Stateful Rules
- You can add iptables rules to detect what state a packet is in.
- This is REALLY useful for FORWARD tables.
- It also, in general, makes your firewall rules more reliable and much smaller, even in INPUT and OUTPUT.
Rules based on network state
- Packets can be in a number of different states:
Basic Stateful FORWARDING
- You are running your firewall machine with 2 network cards, eth0 and eth1.
- Eth0 connects to the internet, Eth1 to the intranet.
- In this regard Eth1 is a gateway for your local network.
Egress filtering
- So far it is normal to see ACCEPT as the default policy for OUTPUT.
- However, this is not as secure as having a DROP policy.
- DROP as the policy in OUTPUT is called egress filtering.
- Although easy to completely mess up it is no harder than INPUT DROP policy.
- It limits OUTPUT packets to only those which you explicitly define.
- It could help reduce hacking attempts, and the spread of viruses.
Complete EGRESS Example
- Configure a non-routing server firewall which runs telnet and http servers. Users on the server can ssh out. Use EGRESS filtering.
/sbin/iptables -F INPUT
/sbin/iptables -F OUTPUT
/sbin/iptables -F FORWARD
/sbin/iptables -P INPUT DROP
/sbin/iptables -P OUTPUT DROP
/sbin/iptables -P FORWARD DROP
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A INPUT -m state --state NEW -p tcp --dport telnet -j ACCEPT
iptables -A INPUT -m state --state NEW -p tcp --dport http -j ACCEPT
iptables -A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A OUTPUT state --state NEW -p tcp --dport ssh -j ACCEPT
Other Firewall Ideas
Discussion
- How would iptables firewall rules, combined with a Linux based router, compare with a custom firewall appliance, such as a Cisco ASA5500?
Discussion
- Here are some past exam questions you should now be able to answer:
Question 1
Show the iptables commands relevant in defining an egress filter allowing only related or established connections, as well as outgoing http, to be accepted and all other egress traffic to be rejected. You can assume egress only involves eth0.
Question 2
Consider the following iptable configuration:
iptables -P INPUT drop
iptables -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --sport ssh -j ACCEPT
Would incoming ssh connection requests be blocked? Give an explanation for your answer.
Linuxzoo created by Gordon Russell.
@ Copyright 2004-2025 Edinburgh Napier University




